Exploiting Visual Appearance to Cluster and Detect Rogue Software
While malware comes in many different flavors, e.g., spam bots, banking trojans or denial-of-service bots, one important monetization technique of recent years is rogue software, such as fake antivirus software (Fake A/V). In this case, the user is tricked into spending money for a rogue software which, in fact, does not aim at fulfilling the promised task. Instead, the rogue software is malicious, might not even have any legitimate functionality at all, and entices the user to pay. However, all rogue software has in common to provide a user interface, e.g., be it to scare the user, or in order to ask for banking credentials, or to carry out the payment process. The following figures show example screenshots of two typical rogue software flavors.
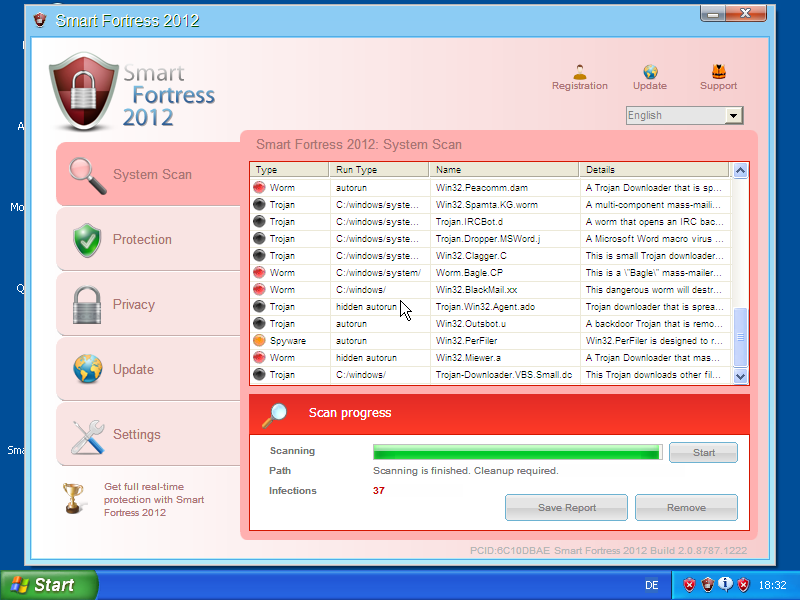
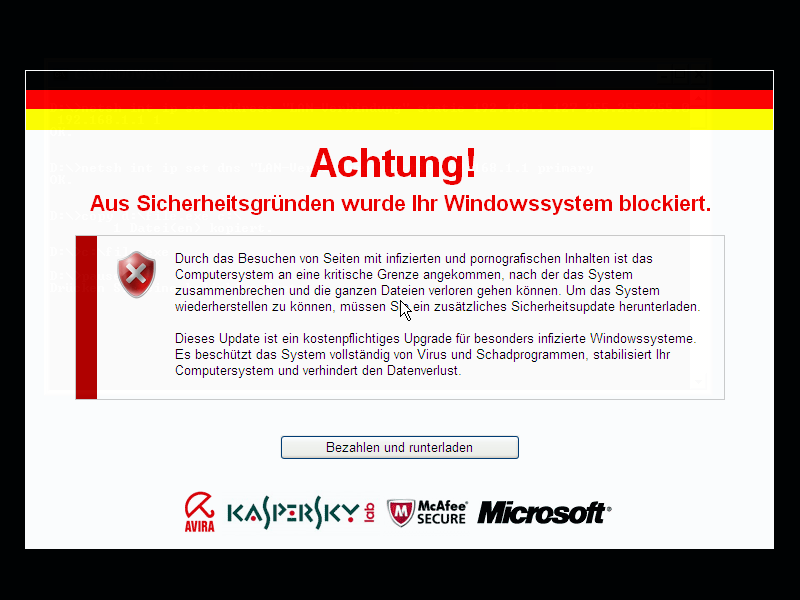
The first displays a Fake A/V user interface, mimicking a benign antivirus application, while the second exhibits a ransom screen (in German), asking the user to pay before the computer is unlocked (in fact the computer appears just visually locked). Especially the later category, ransomware, is considered an increasing threat with more than 120,000 new ransomware binaries in the second quarter of 2012. In addition, referring to the C&C tracking of Fake A/V and ransomware botnets, we observe a significant increase in activity since June 2011.
As rogue software is required to provide a user interface, we aim at exploiting its visual appearance in order to cluster and classify rogue software. We motivate our efforts by the relatively low A/V detection rates of such rogue software, and we aim to complement existing techniques to strive for better detection rates. In particular, we observed that the structure of the user interfaces of rogue software remains constant and can be used to recognize a rogue software family or campaign. Using a perceptual hash function and a hierarchical clustering approach, Christian Rossow and I, we propose a scalable and effective approach to cluster associated screenshot images of malware samples. In short, the main contributions of our work are threefold:
- We provide a scalable method to cluster and classify rogue software based on its user interface, an inherent property of rogue visual malware.
- We applied our method to a corpus of more than 187,560 malware samples of more than 2,000 distinct families (based on Microsoft A/V labels) and revealed 25 distinct types of rogue software user interfaces. Our method successfully reduces the amount of more than 187,560 malware samples and their associated screenshot images down to a set of human-manageable size, which assists a human analyst in understanding and combating Fake A/V and ransomware.
- We provide insights into Fake A/V and ransomware campaigns as well as their payment means. More specifically, we show a clear distinction of payment methods between Fake A/V and ransomware campaigns.
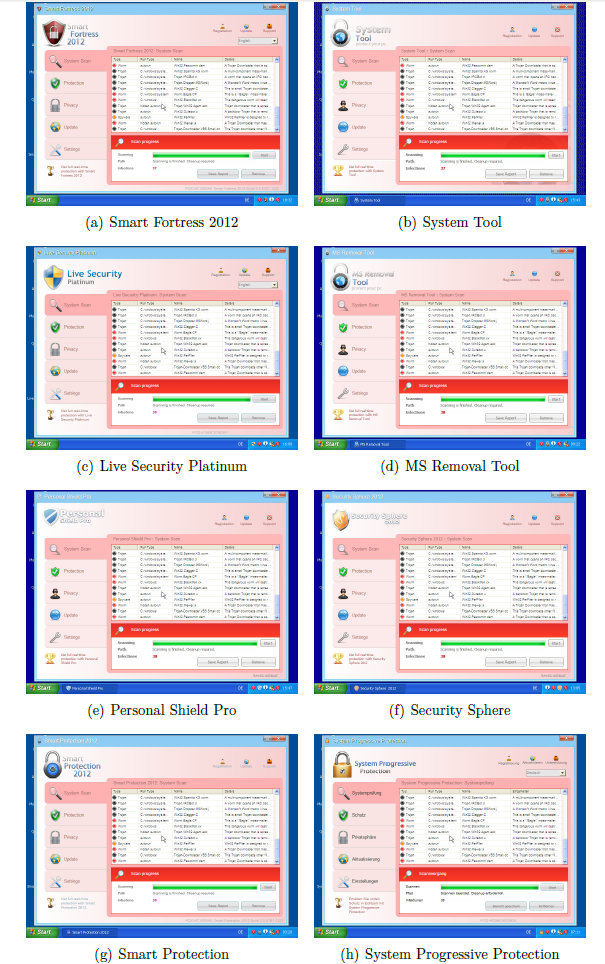
As an example and in order to underline the usefulness of our approach, we used the our visual clustering to enumerate the campaigns that can be attributed to the Winwebsec family. Note the visual similarity among the different campaigns, sometimes it is even difficult to spot the difference. Typically, the campaigns differ in names as well as logos.
I am delighted to announce that our paper was accepted for the security track of ACM’s 28th Symposium On Applied Computing 2013. A preprint of our manuscript for ACM SAC 2013 is available here Exploiting Visual Appearance to Cluster and Detect Rogue Software.