Tracking the Command and Control Activity of Botnets
As part of our research on botnets, we developed recognition techniques for botnet command and control flows, such as CoCoSpot. Obviously, we use these techniques to track C&C channels and their activities. Throughout our analysis period of more than three years, we have seen several botnets come and go. Some botnets have faced dedicated takedowns, such as Rustock, Mariposa, Mega-D, Kelihos and Pushdo, while others cease without further ado.
By help of our tracking means, we are able to classify the activity of C&C channels. The following figure graphs the activity of some 25+ prevalent botnets in terms of consecutive C&C activity by family, as seen and covered by our tracking means, as well as public attention. The x-axis reflects the time period since February, 1st, 2010 until February, 13th, 2013, while the y-axis lists botnet families. A star depicts a dedicated takedown action. Note that, in case of Mariposa and Mega-D, the takedown actions have taken place before the beginning of the time period in this graph. The Mariposa takedown has occurred on December 23rd, 2009, and Mega-D has been taken down in November 2009. In these cases, the stars are placed on the start of the time period in order to visualize the preceding takedown. A thin black line with black markers represents the time period where new binaries are distributed, but none of the binaries exhibit an active C&C channel. Inactive C&C channels are caused, for example, by outdated binaries, unreachable C&C servers or sinkholing (possibly after successful takedowns). The Rustock takedown operation b107 by Microsoft’s DCU is an example of such a successful takedown. Similarly, the Harnig botnet, which is believed to have been the main distributor of Rustock (most likely via pay-per-install), exhibits inactive C&C since March, 2011. This correlates to the time of the Rustock takedown operation. Coincidence?
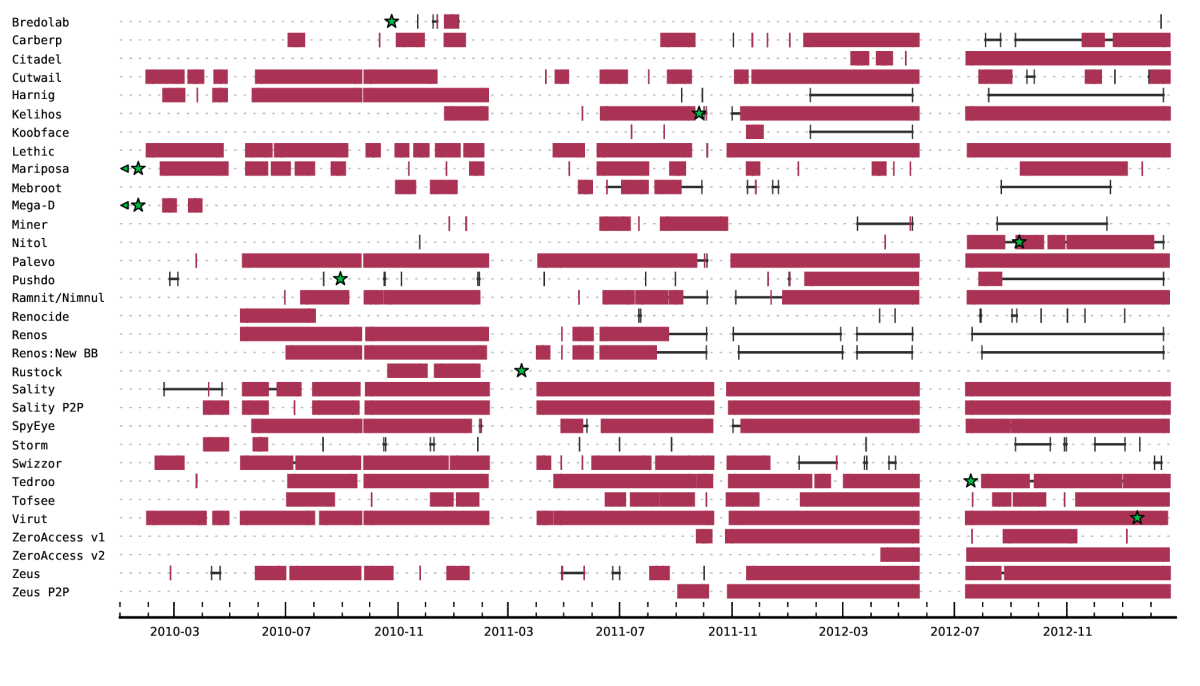
In contrast to inactive C&C, a thick red bar represents the time periods where active C&C communication has been observed, and this is where things get really interesting. Every time I look at this graph, I am astonished by the fact that some botnets manage to operate successfully since several years. Cutwail, Virut, Sality, Palevo and Lethic are mere examples for such long-living botnets. However, their strategies for continued operation differ. While Sality has had a builtin peer-to-peer (P2P) component for years, Virut has experienced the comfort of using just a handful of domains in order to contact the C&C server. In case the domains cannot be resolved, a domain generation algorithm (DGA) kicks in. However, only recently, a takedown operation addressed Virut. Palevo seems to keep it simple, neither P2P nor DGA nor significantly low TTLs on the DNS responses (which could indicate fast flux). Instead Palevo seems to rely on new and migrating domains. Similar to Palevo, Lethic manages to bootstrap its C&C by plain old DNS resolution. These are just some examples of long-lasting botnets with active C&C, most of which have a centralized primary C&C architecture. In contrast to botnets with centralized C&C, several peer-to-peer botnets have emerged. Storm, Miner, ZeroAccess, Kelihos and Zeus P2P exhibit a primary C&C which is based on a P2P network, probably motivated by increased resilience. While Storm and Miner ceased, ZeroAccess, Kelihos and Zeus P2P show significant C&C activity — an observation also covered in our yet-to-be-published research paper on P2P botnet resilience.
On the sustain of botnet takedowns
What do we learn from this? On the one hand, as can be seen in the figure, the takedowns of the Bredolab as well as the Rustock botnet have a long-lasting effect. Although for Bredolab and Mega-D we witness active C&C during up to several months after the takedowns, none of these botnets manage to achieve active C&C communication in the long run. On the other hand, we have seen quite a few botnet families resurrect from takedowns. For example, researchers initiated a takedown of the Pushdo botnet in August 2010. However, even two years after the takedown, we still observe active executions of Pushdo. The Mariposa botnet is believed to have been taken down in December 2009, but we have seen active Mariposa command and control traffic ever since. Similarly, although the Nitol botnets have been taken down in September 2012, many Nitol binaries manage to successfully bootstrap and reach a viable C&C server, because they do not rely on the suspended domains such as 3322.org. In addition, the Tedroo botnet has been addressed in a takedown action in July, 2012. However, again, we observed active C&C communication of the same botnet family just within days after the takedown, continuing for at least three months. Thus, from an observational point of view, the challenge of botnet family takedowns lies in their sustain.
Some botnets even cease without a dedicated (publicly known) takedown of the C&C infrastructure. For example, the Miner botnet has not been addressed in a dedicated takedown operation of its peer-to-peer-based C&C, but its activity diminished significantly after October 2011. Similarly, the Renos botnet has ceased its operation, although possibly after removal signatures of the Renos binaries have been distributed by Microsoft as part of its Removal Tool MSRT. It is an open question as to whether the criminals behind these botnets just moved on to the next botnet. Most notably, the authors of Kelihos/Hlux (some consider Kelihos the successor of Waledac) stick to their botnet and change aspects such as the C&C encryption when faced with a takedown.
While many of the botnets mentioned above have been subject to takedown or sinkholing, it becomes obvious that a successful takedown is by far not an easy process. Bot masters distribute their infrastructure so that a takedown operation requires many different parties to cooperate — a challenging task.
Remarks
Finally, just a couple of remarks: Note that the monitoring time period has been interrupted by maintenance periods, from mid-February to mid-March 2011 as well as end-May to mid-July 2012. Furthermore, the per-family perspective does not always reflect all activity of the correspondings botnets; however, it can be considered a lower estimate. Especially since some families exhibit (lots of) distinct botnets, we certainly do not cover every unique botnet of that particular family. For example, in case of toolkit-based families such as Zeus and SpyEye, several distinct botnets may be formed. In our C&C activity tracking, we restrict ourselves to whole families instead of individual botnets on purpose.